Introduction to The Protocol Reader
Venkatesh Rao
Program Director, Summer of Protocols
In the Fall of 2022, the word protocol was suddenly everywhere. The proximal cause was obvious: fueled, in part, by the highly visible and fractious change of ownership at Twitter, large numbers of people began heading for the exits.
Most of them, of course, were just looking for alternative products or platforms offering roughly the same user experience as Twitter, just with more allied politics and ownership. Many, for instance, fled to Meta’s hastily cobbled together Threads offering. Others fled to Substack or LinkedIn. And a great many simply curtailed their participation in public social media, retreating to cozier private enclaves online.
But a significant minority—amounting to perhaps several million—chose to do something much more creative. Instead of looking for yet another flavor of what they were already used to, they went looking for an alternative technology paradigm. And began discovering a curious class of alternatives to Twitter that described themselves as protocols rather than products or platforms.
They found themselves immediately mired in confusion swirling around both the word protocol and the curious things it was pointing to. What on earth was this Fediverse? Or were you supposed to call it Mastodon? No wait, you were supposed to call it ActivityPub! And what was this Bluesky/ATProto thing? Or this Warpcast/Farcaster thing the crypto crowd was pushing? Or this strange beast called Nostr? Why did “signing up” work in weird ways? What is a public/private keypair, and why do you need one? What does it mean to pick a client, instance, wallet, relay, or host? Why weren’t there single points of entry into whatever these things were?
Intimidated by the arcane facade, many bounced off immediately and returned to the world of platforms to make their peace with the familiar set of choices. But some stayed long enough to give what are now called protocol social media a quick test drive, and acquire rudimentary orientation, situational awareness, and literacy.
Of these, many decided it was not worth the trouble. The convenience, simplicity, and promise of vast global reach offered by traditional social media was much too attractive. But unlike those who had bounced off the surface, they left with a newly educated awareness of options they previously had no idea existed.
Despite these multiple rounds of winnowing, which served as a kind of accidental, emergent marketing funnel, enough people stuck around that the world of protocol social media still found itself dealing with the largest wave of immigration and adoption it had experienced in its brief existence. Protocol technologies are notoriously terrible at marketing themselves (since coherent brand identities and narratives are somewhat at odds with the typically decentralized architectures), so this was a welcome windfall of attention and adoption.
Those who stuck around were slowly seduced by the strange new worlds they were discovering. Worlds characterized by a fundamentally different approach to technology that didn’t just promise to replace one unaccountable authority with another, but offered an entirely different scheme of governance and ownership for true technological commons. An approach that promised to anchor desiderata such as censorship resistance, data rights, anonymity protections, and that elusive holy grail, “decentralization,” not in glib ideological rhetoric, or even the legal assurances of sympathetic political regimes, but in the inviolability of mathematical theorems. They began to acquire a taste for a property of certain technological systems that Josh Stark calls hardness in one of the essays included in this volume, “Atoms, Institutions, and Blockchains.”
To use a phrase many of them would go on to encounter, they had discovered a world whose lighthouse principle was not Google’s don’t be evil, but can’t be evil. A phrase that strikes some as naively utopian and others as more ominous than Google’s motto, but has significant substance no matter how you think about it.
You’re about to embark on a similar journey to those explorers in 2022 (and perhaps you were even among them). This volume is intended to introduce you to a strange new world that has invisibly taken shape all around us over the last fifty years, and is now beginning to alter the very fabric of the world in visible ways—the world of protocols. You may or may not like what you find. You may or may not decide to stay. But for those of you who choose to stay, this volume is designed to help you learn, in the words of Morpheus in The Matrix, just how deep the rabbit hole goes.
By the time you’re done with these 26 essays by 35 authors, which we’ve curated into what is hopefully both an enlightening and absorbing sequence, we are confident you will become protocol-pilled. To be protocol-pilled is to be both literate in the powerful emerging technological idiom of protocols and its associated discourses and, to use a term coined by cartoonist Randall Munroe, nerdsniped by the deeply satisfying lenses, levers, and mental models it offers.
The essays in this volume are the product of the pilot year of a program called the Summer of Protocols, which began in 2022 around the same time the exodus from Twitter was unfolding. The program goal was simple: to study protocols in the broadest sense, from as many perspectives as possible, to see if there is a there there. Were we like the blind men in the fable, in the dark touching different parts of the elephant? Were we chasing a coherence and unity that wasn’t there to be found? Was there perhaps something more universal and coherent lurking beneath a word used for such disparate things as computer networking schemes, climate treaties, hand-washing practices, interactions with royals, treatment of football injuries, medical research design, fire-fighting practices, diplomatic etiquette, and blockchains?
The last of these provided the precipitating motivation. Now entering its third year, Summer of Protocols was initially funded by the Ethereum Foundation, and motivated by a relatively narrow but fiendishly difficult sociotechnical challenge—the problem of consciously “ossifying” the Ethereum blockchain: managing the tension between the desire to keep adding tempting new features and the opposed desire to converge on a minimal reliable functional scope, capable of lasting not merely years or even decades, but a century or longer. We hoped that by studying protocols in the broadest way we could conceive not only would we help an undertheorized subject reach a threshold of critical mass but, via oblique side effects, discover creative new ways to approach unprecedented planetary-scale challenges like managed ossification, climate change, and the rise of AI.
The research and entrepreneurship community that has emerged around the program—an eclectic mix of practitioners and academics, bloggers and artists, hackers, and protocol entrepreneurs from around the world—now has 66 program alumni, and hundreds of more casual participants. The output, of which this volume is a subset, already fills a three-inch binder of printed materials. And more material—in the form of case studies, speculative fiction, artistic explorations, design studies, code, and dozens of seminar videos by both our researchers and invited guests—is rapidly accumulating. You will find all of it on our website (summerofprotocols.com), available open-access, for free, under a liberal open-source license.
We hope you will not just explore the material, but think about ways it can inform or shape your own activities. We hope some of you will even join us in future Summer of Protocols activities, as researchers, educators, institutional partners, protocol entrepreneurs, or even just casual hobbyists. If you’ve ever played with Legos, made music, or geeked out over cool infrastructure, you’ve already been exposed to protocols as a hobby.
As we’ve discovered through two years of experimentation, it’s hard to protocol pill even the most thoughtful person in five minutes. While protocols are not quite as arcane as a bewildering first encounter might suggest, they are also not trivial to wrap your mind around.
If you’re willing to invest the weekend it will take you to get through this book, we are confident we can get you there and that you will thank us for it. The material here is more demanding than an airport bestseller, but requires no specialized knowledge or skills to understand. Let’s get oriented to the material you’re diving into.
The Rise of Protocols
The word protocol in its modern, technologically colored sense, but encompassing more social and cultural usages as well, has steadily gained currency and salience over the last four decades, especially in modern technocratic organizations.
The trend is visible in a Google Books Ngram view, which shows a steep rise in usage starting in the 1970s, with a peak around 2000—corresponding to growing interest in basic internet protocols. After this, usage fell to a high valley, followed by another small peak starting around 2017—corresponding to the crypto boom as well as growing interest in protocol social media and smaller trends like interest in health and longevity protocols. As of 2024, usage appears to be settling at a high plateau.
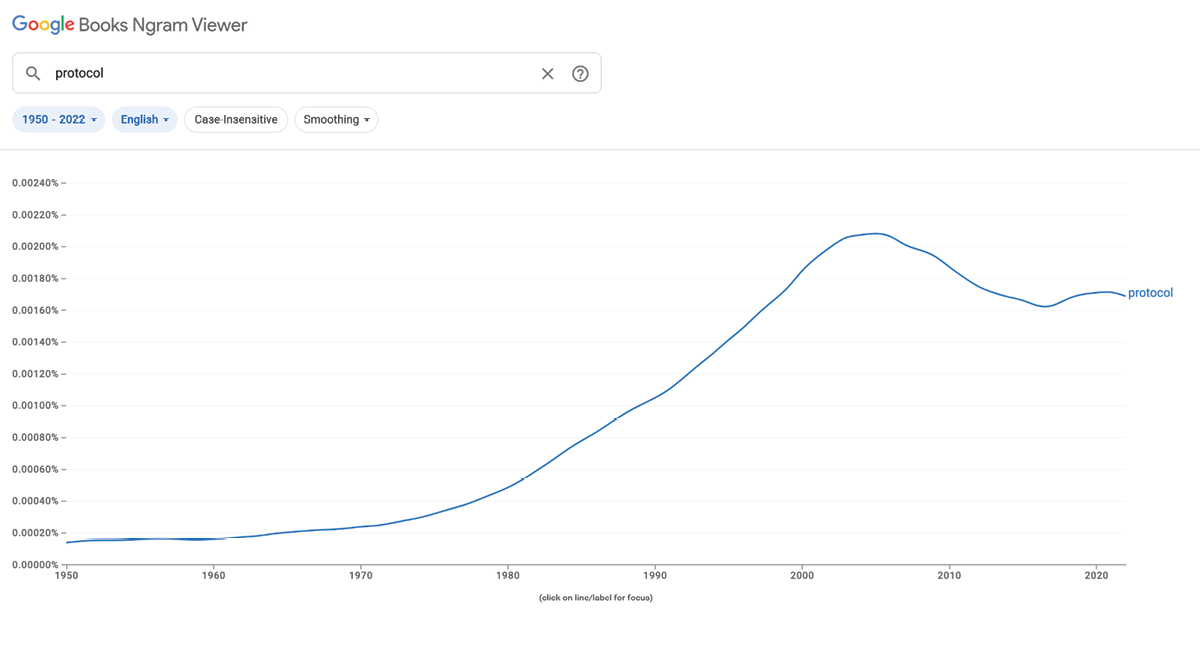
The shape is a classic instance, if radically temporally distended, of that staple of technology analysis, the Gartner hype cycle.1 The build-up has been slow, but inexorable. Protocols—if we may be forgiven a touch of evangelical hubris—are like the mills of the gods: They grind slowly, but they grind exceedingly small.
Two cult television franchises2 give us a clue about what was going on through these decades, as the incidence of protocol traversed this curve. In the original Doctor Who that ran from 1963 to 1989, the word protocol appears in just two episodes out of 695, a per-episode incidence of 0.3%. In the modern run, 2005 to 2022, we find seventy instances in 180 episodes, an incidence of 39%, two orders of magnitude higher!
The contrast is even more striking in Star Trek. The original series that ran from 1966 to 1969 featured zero instances across eighty episodes, while the 1995 to 2001 Voyager series features 176 instances in 168 episodes, a 105% incidence! Similar trends can likely be found in other kinds of shows, such as crime procedurals or medical dramas.
The trend is evident in movies as well. A video montage compiled by Summer of Protocols researcher Kara Kittell3 features a dizzying variety of characters, in movies from a surprising range of genres, talking about protocols.
Even casual sampling of these shows and movies reveals the reason. Over the last four decades, our environment has gotten increasingly technologically structured, sophisticated, and abstract, in ways that cut across traditional institutional boundaries. Computers and software are everywhere. And even where they are not, our behaviors are increasingly protocolized or “by the book”—a result of necessary training in (often counterintuitive) procedural skills without which many kinds of advanced technological agency are not accessible.
Even the stereotype of the “maverick” butting heads with the “system” has evolved—from a relatively low-tech improviser who disregards the notional book to a drunken master who understands the book better than their straight-laced foil. As Geoff Manaugh, author of the presciently titled Burglar’s Guide to the City, argued in a guest talk hosted by the program, the modern burglar often understands the protocols of urbanism better than the insiders who are their nominal stewards. In a world that increasingly comprises protocols, power follows knowledge, not ascriptive authority.4
One result of the shifting environment is that the institutionally anchored “competent man” trope of Golden Age science fiction has evolved into what is sometimes called “competence porn” tropes, showcasing advanced patterns of technological agency increasingly detached from particular institutional contexts. The new tropes are anchored instead in the general technological environment.
Where the bureaucratic hero has mastered a specific set of institutional realities (and is typically helpless outside those realities), the hero of a protocolized world has mastered a general set of technological patterns that undergird not just the internal realities of organizations across the entire planet but even the interstitial spaces between them.
This mastery is marked by a sensitive attunement to what program participant Samuel Chua described as “technology without technocracy.” Such attunement enables the hero to disregard boundaries and cosmetic appearances and, like the awakened protagonists of the Matrix (already a quarter-century old!), engage directly with the protocolized bedrock of our environment. Where the cyberpunk hero was a lowlife maverick outsider who typically had to hack their way to technological agency from an external locus, what we might call the protocol punk hero operates from within a protocolized environment where boundaries separating insides and outsides are increasingly meaningless.
The protocol punk hero is an archetype that merges the 1950s style insider bureaucrat hero5 and the 1980–90s style outsider maverick hacker hero. It is an archetype whose earliest manifestations can perhaps be traced to characters like Andy DuFresne in The Shawshank Redemption, John McClane in Die Hard (the inspiration for Geoff Manaugh’s burglar’s-eye view of built environments), and, of course, Neo in The Matrix. More recent examples can be found in shows like Burn Notice, Mr. Robot, Person of Interest, and recent installments of the long-running Mission Impossible franchise.
When everything is inside the belly of the technological beast, there is no “outside” or “underbelly.” There is only a range of postures of greater or lesser agency that one can adopt while on the inside. The greater the attunement to the protocolized environment, the greater the agency. The greater the attunement to mere technocracy, the lower the agency.
In terms of the popular typologies introduced by Deleuze and Guattari, the protocol punk hero, unlike the bureaucratic hero or the outsider maverick, is master of both smooth and striated spaces, and able to navigate both arborescent and rhizomatic epistemic environments.
Protocol Phenomenology
As the on-screen portrayal of protocols correctly suggests, the phenomenology of protocols is vast. Janna Tay’s essay, “The Phenomenology of Protocols,” and Olivia Steiert’s “Protocols in (Emergency) Time” explore this territory in broad ways, but it is worth highlighting a few key elements.
Slow-but-inexorable is the main “tell” of protocol technologies. In his 2013 New Yorker essay, “Slow Ideas,” physician Atul Gawande noted that simple but powerful ideas in healthcare, such as the use of disinfectants and handwashing, spread characteristically slowly, often taking decades or even a century or more to fully spread across the world.6 Another example is container shipping, a simple idea that took decades to spread across the world, a story that is told in Marc Levinson’s magisterial book, The Box. A third example is industrial safety practices in coal mining, which took nearly two centuries to spread, evolve, and mature into their modern form, a story told in an essay in this volume, “Safe New World,” by Timber Schroff.
Though they arrive slowly, protocols typically install themselves in extraordinarily persistent ways, often turning into seemingly immortal and unconscious parts of our built environment. Their relative invisibility is a second major tell. A lighthouse idea that you will find cited frequently in this volume helped shape the early priorities of our program and has to do with invisibility—philosopher Alfred North Whitehead’s observation:
Civilization advances by extending the number of important operations which we can perform without thinking of them.
The phrase Whitehead advance has become a term of art in our research conversations.
Whitehead advances often take the form of protocols. It took a pandemic to make most of us realize that we possessed disciplined handwashing behaviors, and that at one time they constituted a Whitehead advance in public health. In the United States, for instance, children are now taught that washing their hands properly should take as long as singing Happy Birthday—a protocol that is clever both in its simplicity and in how it coopts a familiar melody (not an accident: there is often an element of musicality to protocol technologies).
Handwashing is the tip of a very large, mostly invisible iceberg. Many of the advances in public health protocols made during the COVID-19 pandemic rested on invisible advances that had already been installed over a century of fighting infectious diseases across the world, much of it lost to living memory. From basic sanitation and quarantine practices, to randomized controlled trials for new drugs and vaccines, to ER protocols for the critically ill, a universe of latent protocols kicked into high gear. And more were added, which will serve us well in the next pandemic.
Few who had experienced the Spanish Flu of 1919 lived to experience COVID-19 a century later, yet the world’s healthcare protocols retained powerful and valuable memories, even if living humans did not. As a result, far fewer humans died. And despite the failure of many individual institutions, the protocols of healthcare held up surprisingly well across the century.
Protocols arrive slowly, and can be incredibly fragile when young, but are remarkably hard to kill once they do arrive. The adoption of protocols, unlike the adoption of more visible, and typically more short-lived, products or ideas, takes time in part because it involves installing unfamiliar and often counterintuitive behaviors in large populations. But once these new societal muscle memories are installed, their largely unconscious nature makes them harder to dislodge than traditional technologies. Email, for instance, one of the oldest internet protocols, has outlived many shallower product- or platform-like alternatives that have attempted to displace it.
One way to understand this is to note that while most technologies are consciously adopted, serving as deliberately employed tools until they become obsolete, protocols tend to enter our lives obliquely, in the form of deceptively simple behaviors, often without even a central technological element, and go on to transform human nature in powerful ways. Where products merely create new kinds of customers, powerful protocols can sometimes create entirely new kinds of humans. Arguably, the very notion of a modern consumer is the product of the early 20th century protocols of industrialization and urban life.
Driving a car, for instance, involves adopting the protocols of road traffic, yet we don’t think of driving behaviors in those terms. We think in terms of buying a car and passing a licensing test. Once we learn to drive, while cars typically become part of our conscious identities, consciousness of traffic protocols recedes into the background—until we attempt to drive in a region with different traffic protocols. In his essay, “Protocols Don’t Build Pyramids,” Drew Austin examines the protocols of urbanism through this lens—as an invisible layer of technologies and behaviors that offer no charismatic symbols of themselves, but instead quietly exercise control over our lives, hiding between the “hardware” and the more visible cultural “software” of cities. Visible only to the sensitive eye, and only as suggestive patterns and regularities in the phenomenology of cities. Chenoe Hart, in her essay “Addressable Space,” casts a similar eye on the addressing schemes that permeate built environments.
Sensitizing oneself to such patterns in different environments, and learning to parse the grammars governing them, has emerged as a critical research methodology for protocols. Many of the essays in this volume take an approach based on inventorying and analyzing the patterns in the emergent phenomenology around a set of protocols (many such inventories can be found on our website). Christopher Alexander’s classic, A Pattern Language, has become a touchstone reference for a significant thread of ongoing research. The resulting insights often generalize much better than those yielded by more traditional objects of inquiry, such as organizations or culturally defined communities.
Protocols create new kinds of humans because the patterned near-invisibility of successful protocols induces a kind of deepening ludic immersion. Such immersion molds human personalities so strongly that we begin to identify with the roles we play in protocols, often without even being aware of them, like fish in water. Visible motifs of powerful technological protocols, such as clocks, watches, smartphones, and cars, can come to define the personalities of individuals and even entire cultures. But the most important parts are typically invisible. For example, while clocks and watches are ubiquitous and highly visible, they are the tip of the iceberg of time protocols in modern life. It is easy to miss the myriad invisible ways in which clock time structures our lives, from train schedules and norms of scheduling meetings to begin at half-hour boundaries, to the structuring of work and leisure hours by calendars with roots in ancient religions.
The upside of such molding is that we can become highly skilled and acquire de facto superpowers without realizing it. To cite a reference that has been popular in our conversations, protocols often instill behaviors the way Mr. Miyagi did in The Karate Kid. Daniel-san acquires karate skills without realizing it, practicing wax-on-wax-off behaviors. The downside, of course, is that their unconscious nature can make protocols powerful mechanisms for coercive control and induced self-destruction.
In her essay on the history of time cultures, “Control and Consciousness of Time,” Saffron Huang dives deep into this phenomenon, around possibly the most powerful class of protocols in our world—those relating to timekeeping.
Less obviously, such ludic immersion with all its positive and negative potentialities is characteristic even of protocols that are mostly cultural in origin, such as those of organized religion. In her essay, “The Protocol System Experience,” Angela Walch takes a broad look at what it means for humans to be unconsciously immersed in protocols, and the often heroic efforts that may be required to break out of them when they begin to fail.
Arguably, we only become aware of the vast majority of protocols when they fail, making us conscious of the patterns of control they embody. Nadia Aspourohova, in her essay, “Dangerous Protocols,” extends arguments first broached by Alexander Galloway two decades ago in his early seminal book, Protocol: How Control Exists After Decentralization.7 Through exploring the ways protocols can become oppressive and destructive, Nadia’s research inspired what has since become both a term of art and a research technique in our program—the Kafka protocol: a speculative protocol that is the absolute worst one conceivable for given circumstances.
It turns out that the thought experiment of Kafka protocols—which some real-world protocols such as TSA airport security approximate—is a surprisingly useful diagnostic tool. In her account, Nadia suggests two other categories of protocols—Whitehead protocols, protocols that represent Whitehead advances and embody net benign and positive patterns of control, and Bartleby protocols, named for the Melville short story, where agency can only be found through inaction and passive resistance.
From Tradeoffs to Tensions
When the Summer of Protocols program began in the fall of 2022 as a pilot study involving half a dozen of us in the Ethereum ecosystem—and which resulted in the essay, “The Unreasonable Sufficiency of Protocols,” included in this volume—we had no idea if there would be a there there. We struggled to come up with a working definition of the word protocol, and to classify a bewildering array of candidates as protocol or not a protocol. It was genuinely challenging to try to distinguish the term from the universe of similar terms (many of which had their vociferous champions)—API, algorithm, platform, norm, standard, tradition, ritual. Drew Austin proposed a useful test of rigor—does your idea suffer if you try to express it without using the word protocol? Does the term add clarity or muddy matters?
The story of the evolution of our definitions (plural) of the term is revealing. The definition we started with, which you will find in “The Unreasonable Sufficiency of Protocols,” is from Ethereum researcher Danny Ryan:
A protocol is a stratum of codified behavior that allows for the construction or emergence of complex coordinated behaviors at adjacent loci.
This definition has now been debated, challenged, rejected, fought over, adopted, ignored, extended, restricted, and generally tortured with relentless energy by dozens of strongly opinionated minds over two years. In several of the other essays, you will find many competing definitions.
In hindsight, each of these conversations, which were often frustrating in the moment, represented steady and, dare we say, convergent progress. Our conceptual understanding steadily improved, as did our ability to draw useful and provocative boundaries.
Through our arguments, we bootstrapped each other into the beginnings of protocol literacy, protocol pilling and nerdsniping each other in a hundred different ways, and collectively muddling through to a rough consensus around what we were talking about. A recent fruit of this process is a definition we’re enamored of:
A protocol is an engineered argument.
This definition was inspired by a definition of the word tension proposed by Tim Beiko, one of the directors of this program:
A tension is a tradeoff plus a conflict.
This definition emerged from a week-long futures workshop held as part of our 2024 program in collaboration with Edge City, an ongoing experiment in virtual urbanism, and 0xParc, a protocols research collective.
In one exercise, participants collected “tension cards” from each other—for example “ossification vs. adaptability” or “regionalism vs. nationalism”—and imagine futures progressively constrained by them. The activity worked beautifully and led to some fascinating output. The Tensions Game, as we call it now, has become a key research tool of the program. The game itself is protocol-like: instead of being choreographed top-down via visioning prompts and scaffolding, the conversation is driven by a peer-to-peer exchange of constraints in the form of digital trading cards.8 It turns the insight behind the joke, “you’re not in traffic, you are traffic,” into a generative collective-visioning mechanism, and protocolizes Frederik Pohl’s famous dictum:
A good science fiction story should be able to predict not the automobile but the traffic jam.
Every successful protocol, arguably, is the result of successfully anticipating some sort of traffic jam, and presciently engineering mechanisms to manage the underlying tensions. Almost everything around us, in technologically modern environments, comprises “engineered arguments” that resemble urban traffic in their phenomenology.
The reason this happens, as Tim likes to observe, is that most people intuitively imagine the future to be “the current world, plus their pet thing.” In reality, the future emerges as a traffic jam of multiple things that are changing in unexpected ways simultaneously, driven by actors with different priorities and headed towards different destinations, creating emergent tensions that all must learn to manage.
The Tensions Game helps build perhaps the important element of protocol literacy—the ability to navigate multiple things changing at once, not all of which you are able to even observe, let alone control. This literacy is primarily social, not technical. Unsurprisingly, even experienced architects who have engineered important protocols can lack this literacy, while seemingly inexperienced “lay” people sometimes just intuitively “get” it.
This notion of a tension is a subtle level-up of the more familiar engineering notion of a tradeoff. Where tradeoffs precipitate decisions, which often enjoy the benefits of finality once made, tensions describe dynamic states that require ongoing management and can call for sophisticated social skills. Unlike the epic heroes of antiquity, or even cyberpunk heroes, protocol punk heroes are rarely lone wolves. Instead, they often exhibit remarkable social skills. Their uncanny protocol-whispering abilities often rest as much on social engineering skills as on technical engineering or architecture skills. And it should come as no surprise that protocol criminality too, of the sort involved in charismatic cryptocurrency heists, or the sorts of modern burglary profiled by Geoff Manaugh, usually involves sophisticated social engineering.
Tensions manifest strongly in protocol-based technology ecosystems like Ethereum where no single person is in charge and many actors are in a state of continuous, stylized punk-on-punk conflict—conflict that can be incredibly generative if managed well and incredibly destructive if managed poorly.
Unlike traditional technologies created by private corporations, governments, or even open-source communities, where an individual auteur architect or engineer might powerfully shape major tradeoffs by fiat and with finality, protocols tend to evolve through, and as, structured arguments that no one actor can dominate. Protocols evolve as moving traffic jams.
Blockchain protocols, of course, exhibit this property in particularly clear and legible ways, with key design decisions being shaped by technical, political, and social arguments among actors whose influence can be measured precisely in terms of the software infrastructure or cryptoeconomic assets they control. A subtlety worth noting: in blockchain protocols, operational control matters more than nominal ownership or authority, as the common phrase not your keys, not your coins highlights.
A major component of the work of protocol whisperers is to manage constantly shifting tensions at an ecosystem level, rather than within a single organization. Often the only levers available are soft personal authority earned through a history of contribution, trusted relationships with allies on many sides of many active arguments (undermining the naive understanding of blockchains as trustless in some cosmic and absolute sense), and, perhaps most importantly, a strong sense of the collective memory of an evolving commons.
The authority of consensus memory is perhaps the closest thing protocols have to a source of continuously renewable legitimacy. The evolution of protocols can be seen as ongoing arguments about what features to enshrine in the protocol itself and what associated narratives to enshrine in the meta of the protocol, to borrow a term from gaming. Stewards of these narratives play something like an intercessory role in the evolution of protocols, mediating relationships of all actors to the evolutionary history that came before them. A commonly held tenet is that a deep sense of history is necessary—without a traditionalist’s attachment to that history—and almost sufficient for effective protocol stewardship.
Not surprisingly, the relationship between protocols and memory turns out to be a deep and important topic, one explored in Kei Kreutler’s essay here, “Artificial Memory and Orienting Infinity.” The things you choose to remember about the history of a protocol arguably constitute your revealed preferences about how you think it ought to evolve in the future. The things a protocol itself remembers is some function of all the things individual participants in it remember and all the traces their behaviors leave behind in the material substrates it touches.
The infinity in Kei’s title points at an important feature of protocols. In the protocol paradigm, the game of technology becomes what the philosopher James Carse called an infinite game—one where you play to continue the game rather than to win. This does not mean that protocols are immortal, or that immortality is a desirable feature. Nor does it mean that protocols preclude competitive vigor or radical changes. As Sarah Friend argues in her essay, “Good Death,” protocols in fact demand a significantly more evolved and actively conscious attitude towards mortality, aging, and yes, death. And as Rafael Fernandez demonstrates in his essay, “Welcome to the Swarm,” powerful protocols can induce some of the most intense and generative kinds of competitive environments, capable of driving innovation and evolution far faster than either traditional markets or top-down organizations. In a similar vein, David Lang notes in his essay, “Standards Make the World,” that protocols and standards are:
Neither state nor market, but essential to both.
Protocols are perhaps best understood as technologies that self-consciously aim to embody the spirit of biological evolution. All technology has an evolutionary character of course, as Brian Arthur demonstrates in his seminal book The Nature of Technology,9 but protocols, as engineered arguments, are evolution-aware technologies that attempt to internalize their key ongoing conflicts in structured and stylized ways, without necessarily “solving” them.
In protocol design and architecture conversations, a truly remarkable amount of conscious and active attention is devoted to things like selection pressures, incentives, red-teaming, and modeling of emergent equilibria. Unlike the engineer in a private corporation, or the bureaucrat in a hospital or a government agency, the protocol whisperer must simultaneously think like an Organization Man, a central banker, a hacker, a market maker, and a military strategist.
This is obviously not easy, and good protocol whisperers are rare and highly valued. But the skills necessary are becoming increasingly visible, imitable, and teachable. The rising level of protocol-whispering abilities is perhaps the best evidence that we are rising to what Stewart Brand proposed as the central challenge of the modern human condition:
We are as gods, and might as well get good at it.
Awareness is becoming evident in traditional technology discourses. For instance, in a classic 2014 commencement address, Only Openings,10 designer Frank Chimero employs an evocative pair of stories drawn from wildlife management protocols at Yellowstone National Park as allegories for good and bad philosophies of technology. As an example of a bad approach, he cites the near-extermination of the gray wolf in the American West by park rangers in the 19th century at the behest of ranchers, which critically destabilized the ecosystem. As an example of a good approach, he cites the more recent case of a similar issue with bears, where rangers began to successfully manage tensions involving bears, rather than attempting to “solve” the bear problem “once and for all.”
Such thoughtfulness is rare, as we continue to discover in our ongoing research. Two 2024 projects, on forest fire management in California and shoreline adaptations in response to sea-level rise in Brooklyn (material on these projects can be found on our website), discovered, unsurprisingly, that the “wolf extermination” approach is far more common than the “bear management” approach. Misguided attempts to solve problems “once and for all” are the default. Efforts to create the right engineered arguments are the exceptions. Playing to win is the norm. Playing to continue the game is rare.
The pluralist infinite-game idea of a protocol as an engineered argument can be contrasted with a complementary “playing to win” definition of an API11 suggested by Tim Beiko: an engineered agreement. Unlike a protocol, an API can be, and usually is, the design outcome of a fiat perspective that aims to solve a problem once and for all, to serve the interests of a single dominant actor. And that perspective is often motivated by a play-to-win mindset. Many corporations and even open-source projects publish such play-to-win APIs relating to their products or platforms. In an increasingly software-eaten world, we often talk of jobs being “below the API,”12 hinting at the natural disposition of the API as an architectural pattern embodying centralized control.
While there may be internal arguments and debates around APIs, typically a powerful architect or group has final say. Underlying tradeoffs are, in corporate-speak, owned by specific individuals or workgroups and never rise to the level of live open-ecosystem tensions managed in, and by, a commons. Internal victories by powerful actors within organizations or communities turn into predetermined external victories at the level of technological ecosystems. These then end up being governed by fragilizing “wolf extermination” philosophies that drive incredibly valuable natural and technological commons to their destruction. In his eponymously titled classic 1998 book, James Scott called this tendency seeing like a state, and the associated technological ideology authoritarian high modernism.13 While the book is increasingly popular in technological circles, contributing to the generally growing awareness and literacy, in protocol-oriented technological circles its lessons are everyday lived realities.
In the world of protocols, authoritarian high-modernist individuals and organizations, able to exercise unchallenged authority and impose play-to-win finite game philosophies, are often termed BDFLs—benevolent dictators for life—a term that first emerged in the Python community to describe the inventor of the language, Guido von Rossum. The term is nearly always employed ironically. Unlike most powerful corporate technologists, such as Steve Jobs, von Rossum famously didn’t want to be a BDFL. But in traditional technological paradigms, BDFLs, whether eager and willing like Steve Jobs and Linus Torvalds, or reluctant, like von Rossum, often have no choice but to play the role. The underlying approach to building technology requires the presence of BDFLs. The seeming indispensability of BDFLs often leads people to the tempting conclusion that the very nature of technology calls for such a source of charismatic authority. The traditional theory of technology is what we might call a Great Man theory of technology.
Protocols though, as engineered arguments, appear to have an unreasonable capacity to evolve coherently without the need for a fiat authority, and make use of the talents of exceptional individuals without becoming vulnerable to their caprices or blindspots. Or to make a stronger statement, they resist BDFLs. Even ones with historical claims to fiat authority.
Of course, many step up and play leadership roles at various times around specific transient challenges, but modern protocol ecosystems resist any single individual becoming a linchpin—a persistent single point of human failure—no matter how benign or positively disposed to the health of the ecosystem they may be. The presence of linchpin individuals is often viewed as being as dangerous as capture by a hostile adversary. Many of these issues are explored in depth in Trent van Epps contribution to this volume, “Capital and Enclosure in Software Commons.”
There are also non-human single points of failure (SPOFs). In a thoughtful critique, Moxie Marlinspike, co-creator of the Signal messaging protocol, pointed out the many SPOF vulnerabilities in the Ethereum ecosystem.14 In the worst cases, they can lurk unseen until they cause the unexpected fatal collapse of a valued protocol.
In well-managed protocols, SPOFs are broadly recognized, consciously managed, gradually mitigated, progressively moved to less and less critical loci, and in the best cases, eliminated altogether. The threats they represent are slowly reduced from existential to manageable to non-existent. SPOFs, both human and non, are typically a major focus of the ongoing engineered argument that is the meta of a protocol. This is true not just of Ethereum, but all thoughtfully stewarded modern protocols. The Signal protocol itself, for instance, while not invulnerable to attack, any more than Ethereum, is less subject than competing messaging technologies to caprices and whims of any single individual or organization.
One reason we do in fact see many examples of healthy protocol ecosystems, full of people who possess not just appropriate skills, but appropriate sensibilities, is that there is a growing loyalty to the paradigm of protocols, beyond any loyalties to specific embodiments of particular technical or social ideas. The idea of end-to-end encryption (E2EE), for instance, has been firmly installed in our collective technological consciousness, regardless of whether specific projects like Signal live or die. The set of ideas that make blockchains possible are here to stay, regardless of whether Bitcoin or Ethereum survive. The protocol paradigm is here to stay.
New Discontents
Discontent with prevailing technological paradigms and the institutions and social paradigms associated with them is, of course, neither new nor rare. Neither is the impulse to exit from them. What is rare is for the impulse to find a foothold in a meaningful alternative paradigm—one with a set of powerful ideas clearly different from the ideas sparking discontent and ideas that have enough coherence and validity to them that we can expect them to survive in the long term, even if particular embodiments don’t survive.
The good news is that protocols do, in fact, represent such a paradigm. They really are an alternative to the paradigm represented not just by traditional social media, but by nearly all industrial-era technologies.
To answer our own question from the beginning of the program, a growing number of us are now convinced, two years in, that not only is there a there there to protocols, it is in fact much more substantial than the prevailing technological paradigm.
The bad news? This new paradigm comes with its own new causes for discontent. The protocol paradigm only promises alternative questions and answers, and different sources of reassuring hardness to bet on. It does not make any promises about satisfying items on whatever ideological checklist you might be bringing with you. Protocols, honestly represented, do not promise that you will face no problems or discontents—only that they won’t be the same old discontents that leave you feeling trapped in the traditional paradigm. They don’t promise a tension-free existence, where all conflicts are magically resolved. They only promise interesting new tensions and an interesting new meta of engineered arguments to manage them.
During the 2022 exodus from Twitter, many immigrants to protocol media reacted with confusion and incoherent expectations upon encountering deeply unfamiliar realities lurking beneath deceptively familiar user experiences. They wanted the comforting affordances they were used to on centralized media. Many found they could not stomach the alien realities—realities that shattered naive utopian expectations, but in ways that bewildered rather than disillusioned, and disoriented rather than infuriated.
For instance, many demanded that mechanisms they were used to—“following,” “muting,” “blocking,” “reporting abuse”—work in familar ways. They tried behaviors and tactics learned on centralized media—such as drives to “deplatform” or “cancel” ideological adversaries—and discovered to their dismay that their tactics either didn’t work at all or had unexpected and confounding results. Tactical skills, hard-won over a decade of culture-warring experience with centralized social media, turned out to be, to use the physicist Paul Dirac’s famous phrase, not even wrong for protocol social media. Some tactics they had mastered, it turned out, had been engineered out of the argument altogether. Other tactics, which they did not understand, had been engineered in, and were driving battles they could make no sense of.
Upon learning that some of their expectations were simply mathematically impossible to provision on protocol media, many reacted with disbelief, anger, and frustration. Surely it was possible to comprehensively block a troll in a guaranteed way? To truly censor an unconscionable view?
Those who arrived full of eagerness to live by what they thought were the absolute principles of the new paradigm encountered disappointment as well. Instead of a lofty and absolute commitment to the principle of “decentralization,” for instance, they found arcane conversations about “sufficient decentralization” constrained by hard-edged technical tradeoffs rather than insufficient ideological fervor. Fraught conversations around anonymity were replaced by new conversations about “KYC regulations” and “Sibyl resistance.”
Both unconscious partisans of the old and diehard ideologues of the new found that they had to manage the tensions of the protocol with a pragmatic and collaborative spirit.
Many experienced an even more unsettling kind of meta-anger and meta-frustration: They discovered that not only was there no way to address their grievances, there wasn’t even anywhere to direct them. While organizations, software products, and individuals associated with a protocol might offer ready and tempting targets, they were not meaningful targets. They had no ability to override the mathematical laws at the root of many grievances. At best, you could hope for the limited satisfaction of imposing your preferences locally or dethroning an influential individual, organization, or software element within a protocol’s ecosystem.
When it comes to protocols, sticking to any kind of ideological hardline position cedes agency to those willing to participate in the engineered arguments. There is no winning move, and the only way to continue to play is to recognize that you’re not in traffic, you are traffic.
Faced with this reality, many, as you might expect, bounce off of protocol social media. Many discover that they have much more of an authoritarian streak than they want to cop to and are unconsciously or not looking for a more global, absolute, and totalitarian imposition of their preferences than protocol social media allow. The necessary affordances are simply missing.
To partisans of protocol media, of course, these “missing” affordances, far from representing bugs or incompleteness, are the defining features. Protocol media, in many ways, are defined by what you can’t do. Ways in which you can’t be evil. Not because some unaccountable authority prohibits it, but because the math says so. The phrase “code is law” has become a bit of a cliché precisely because in protocol media, there is a good deal of substance to it.
This substance, it turns out, is more than just an inconvenient truth for some with deeply held political convictions. It is an unconscionable one. To certain political sensibilities, being told that certain behaviors are mathematically impossible to police by design is a moral affront. It provides sufficient cause to advocate for the outright banning of protocols that do not admit familiar modes of imposition of moral authority. It elevates a subset of modern cryptographically secure protocols to a rarefied tier of technologies—alongside nuclear power, AI, and genetic engineering—that attract efforts to impose blanket bans on their existence and continued development.
The world at large is starting to come to terms with a profound realization: The technologies underlying protocol social media, such as end-to-end encryption and blockchains, and the powerful composable and distributed systems they allow us to build, do not conform to familiar moral expectations and intuitions. The laws of the strange new worlds of protocols cannot be bent to conform to those expectations or intuitions. They address old discontents, but also trigger new ones for which no satisfying answers may exist. We must either choose to trade old discontents for new ones, and proceed to explore these worlds on their own terms, or retreat from the adventures they promise. And if we choose to explore, we must do so with the same sense of heightened responsibility we bring to other potentially dangerous technologies.
We hope this book will convince you to choose exploration over retreat. The structure we have adopted aims to take you from protocol-curious to protocol-pilled; literate and empowered to act in ways you perhaps did not realize were possible. But if instead, we provoke powerful new discontents for you, and turn you into a committed critic, devoted to alternative paradigms, we’ll still consider that a win. If a discourse is engineered right, a literate adversary can sometimes add more value than an ignorant ally.
In Part 1, Seeing Protocols, you will find a set of essays that will help sensitize you to the protocols all around us, and the patterns of phenomenology they present. In Part 2, Arguing Protocols, we will introduce a variety of analytical and conceptual frameworks designed to help you think about protocols. In Part 3, World Engines, we have a set of application-oriented essays from a variety of domains that aim to build your basic “protocol muscles,” and intuitions, enabling you to make decisions and choose behaviors with a literate awareness. Finally, in Part 4, Living With Protocols, we have a set of wide-angle essays that offer broad views of the world through protocol-tinted glasses, and two speculative fiction pieces that attempt to envision protocolized futures.
The structure is one some of you may recognize—it is loosely based on John Boyd’s OODA loop (observe, orient, decide, act), itself a kind of epistemic protocol. Our goal with this volume is to help you install a basic protocol-pilled OODA loop in your thinking, and learn to see the world through it, as well as develop what is sometimes called Fingerspitzengefühl—a finger-tips feeling—for this fascinating subject.
Once you’re done with this book, if you want to know more, and join us on our future adventures, we encourage you to check out our website, summerofprotocols.com, and explore the array of resources and opportunities to participate you will find there.
Afterword: Towards a Hardened Commons
When the Summer of Protocols began, something like a nascent field of protocols was already taking shape. The goal of the program was to pave the cowpaths and make the contours of the emerging field legible, both to those who haven’t yet paid attention to protocols and to those already deep in the world of protocols who have perhaps not had a chance to reflect on the broader significance of their work.
In this limited aim, we believe we have already succeeded. Fertile, if fragile, conversations have now taken root in a small but growing community that concerns itself with broad questions about protocols, beyond the specifics of particular domains like blockchains, climate, or healthcare, or the specific priorities of particular academic fields that may concern themselves with particular conceptual aspects of protocols. The conversations have sparked artistic, research, and entrepreneurial initiatives.
How do we proceed beyond this limited aim, to both broaden and deepen these conversations, and strengthen both the praxis and poiesis of inquiry into protocols?
In the last two years, in shaping this program, we have sought inspiration from many sources. We looked at influential loose fellowships such as the Vienna Circle and the Bloomsbury Group from a century ago. We looked at influential events and conferences like the Solvay conferences in physics, the Macy conferences in cybernetics, and the International Geophysical Year in earth science. We studied the early genesis of modern fields like economics, information theory, AI, cybernetics, STS (Science and Technology Studies).
We took cues from examples of broad cultural catalysis, such as the rise of modern science fiction under the stewardship of Astounding magazine in the 1930s, the development of countercultural technology discourses sparked by the Whole Earth Catalog in the 1970s, the role of the O’Reilly publishing in the emergence of the maker movement, the rise of a distinct entrepreneurial culture in Silicon Valley shaped by VC bloggers, and the recent efforts, spearheaded by Stripe, to establish the field of progress studies.
Any attempt to create a new field and an associated set of discourses, of course, is necessarily both a political project and a practical one. On the practical front, there is the question of prioritization and emphasis in allocation of scarce resources. Should the focus be on foundational theory or practice? On STEM aspects or humanities aspects? Should research stay relatively close to narrow motivating priorities (in this case the sociotechnical problems of blockchains and cryptoeconomics) or follow promising trails wherever they lead?
We’ve grappled with these tensions over two years and attempted to place reasonably hedged bets. While this volume profiles the theoretical and historical research that resulted, other output from the program focuses on practical applications, art, and pedagogy. Depending on which aspect of our work we are talking about, we speak of protocol studies, protocol science, protocol entrepreneurship, or protocol evangelism. This emerging field doesn’t have a name yet, and perhaps it does not need one. Or perhaps it can have more than one.
In terms of organizational forms, coming from the world of blockchain protocols, we have a natural bias towards the patterns of organization common in that domain—“working in public” with high openness, bottom-up funding using innovative mechanisms such as quadratic voting, decentralized autonomous organizations, and primarily virtual collaboration supported by overengineered in-person events.
While we are open to traditional approaches, like working through think tanks, academic departments, disciplinary associations, and conventional funding models, we aim to do so by building bridges and partnerships. We hope to build a coalition of diverse partners unified by a shared interest in protocols. To this end, if you and your institution possess strengths complementary to those of our program, we welcome collaboration overtures. We aim to pursue an eat-your-own-dogfood approach, and catalyze a protocol to study protocols.
On the political front, any set of priorities, regardless of how reasonable and well-motivated they may seem to us, will necessarily pose a challenge to the priorities and paradigms of existing fields. Over the last couple of years, a few observers have sincerely questioned the need for a new field, and argued that the concerns are already well addressed by existing fields. Various people have proposed a variety of existing fields, such as social psychology, cybernetics, STS, systems theory, critical theory, and economics, as the natural home for the discourses around protocols that we hope to catalyze. The same is true on the more practical front. Does the idea of protocol entrepreneurship, which we have been attempting to codify, add anything to entrepreneurial playbooks that already exist, such as the Silicon Valley model, social entrepreneurship, intrapreneurship, or public sector entrepreneurship? Do efforts to seek general principles across domains weaken focus in particular domains? Does an effort to create a general science of protocols weaken, rather than strengthen, efforts to establish specific climate protocols or encryption standards?
Such critical considerations are of course valuable and necessary. While such considerations are sometimes raised in bad-faith, driven by an impulse to “capture” a new discourse (a concern we are particularly alive to, since capture dynamics are a foundational topic), most are well-intentioned and sincere, and worth serious attention. Any effort to create a broad new discourse, underwritten by new patterns of individual and institutional attention, risks turning into an exercise in intellectual hubris if it refuses to entertain such considerations.
At the same time, however, there is a risk of a genuinely valuable new pattern of priorities, a new orientation, being torn apart by such centrifugal forces, even if they are sincere and well-intentioned. How can one balance the tension between being responsive to valid critical concerns, and the need to give a new orientation a chance to prove its worth?
A weak way to manage such tensions is to simply declare an ideologically colored agenda by fiat, and attempt to brute force a critical level of momentum through some mix of heavy investment of resources, intensive zero-sum marketing and evangelism, and the erection of heavily policed turf boundaries.
We believe that this approach would be not only misguided and doomed—and typically the result of a curse-of-resources problem we are glad we do not suffer from—but would be deeply ironic in relation to the specific themes of protocols. The je ne sais quoi of protocols, after all, is an ineffable quality of openness, connectivity, serendipity, emergent resources, peering, heterogeneity, and pluralism. It would be strange indeed to attempt to establish a fortress-like “Center for Protocol Studies” that wages war from behind high, impenetrable walls on any competing claims to space of ideas.
Our approach in the Summer of Protocols program—one that, given the limited resources at our disposal, is really the only one available to us—is based on foundational curiosities and a deep sense of history rather than missionary manifestos, on seduction through nerd-sniping and pilling rather than marketing and overt evangelism, and on radical openness and mutualism over exclusionary control. Beyond hardening our activities against capture or co-option by narrower agendas, and doing our best to articulate, in honest but unapologetic ways, the opinionated tastes we are bringing to our curation and catalysis efforts, we aim to keep our role small and limited, and indeed, shrink it over time.
As the discourses we aim to catalyze become self-sustaining, hopefully supported by a growing number of individuals and organizations with a variety of perspectives and motives, the Summer of Protocols program, we hope, will become unnecessary. The goal of the program, in other words, is to create a hardened commons around the art and science of protocols, and then stop.
This goal, we believe, is one that will float all boats and best support the vision of bringing powerful new ideas and capabilities to bear on the opportunities and challenges facing the world. We hope this volume, as an early contribution to this emerging commons, will help jumpstart this process.
-
1. A popular model of how technologies get adopted. See en.wikipedia.org/wiki/Gartner_hype_cycle.
-
2. For details: forum.summerofprotocols.com/t/protocols-in-doctor-who-and-star-trek/243.
-
3. Kara Kittel, “Protocol supercut,” www.youtube.com/watch?v=HiUcxUC9Z2c, or the extended cut, www.youtube.com/watch?v=uSOw-hulg6s.
-
4. Geoff Manaugh, “Codes of Entry: Burglary, Architecture, and the Protocols of ‘Nakatomi Space,’” www.youtube.com/watch?v=pK7U2IrPETQ.
-
5. See Merve Emre’s 2013 essay, “Bureaucratic Heroism.” www.nplusonemag.com/online-only/online-only/bureaucratic-heroism/.
-
6. Atul Gawande, “Slow Ideas,” New Yorker, July 22, 2013, www.newyorker.com/magazine/2013/07/29/slow-ideas.
-
7. Alexander Galloway, Protocol: How Control Exists After Decentralization (Cambridge, Mass.: MIT Press, 2004).
-
8. Via an app called ZuPass, developed by our partners 0xParc (0xparc.org), using a rather esoteric class of zero-knowledge protocols.
-
9. Brian Arthur, The Nature of Technology: What It Is and How It Evolves (New York: Free Press, 2009).
-
10. Frank Chimero, “Only Openings,” May 14, 2014, frankchimero.com/blog/2014/only-openings/.
-
11. Application programming interface, a kind of technical surface around a technological object designed to allow other technologies to interact with it.
-
12. You can find an interesting short story with this title by Stephen Bailey, from our 2024 cohort, at summerofprotocols.com/pills/below-the-api.
-
13. James C. Scott, Seeing Like a State: How Certain Schemes to Improve the Human Condition Have Failed (New Haven: Yale University Press, 1998).
-
14. Moxie Marlinspike, “My first impressions of Web3,” January 7, 2022, moxie.org/2022/01/07/web3-first-impressions.html.

